Encryption-Techniques A-20 Comprehensive Guide
In today’s world of ubiquitous data transmission and storage, encryption has become an indispensable tool for protecting sensitive information from unauthorized access. Encryption is the process of transforming plain text into cipher text, which is unintelligible to anyone without the key to decrypt it. There are various encryption techniques that are used to achieve this goal. In this article, we will discuss some of the most commonly used encryption techniques and their strengths and weaknesses.
Introduction:
In today’s digital age, encryption is a crucial aspect of securing sensitive information, communication, and data. Encryption is the process of converting plain text into cipher text so that only authorized users with a decryption key can read the message. Encryption techniques have evolved over time, and there are numerous algorithms and methods used to protect data in transit and at rest. In this article, we will discuss various encryption techniques and their applications.
In the digital age, data security has become increasingly important. Encryption is a key tool used to secure digital data by encoding it in such a way that only authorized parties can read it. Encryption has been around for centuries, but the techniques used today are much more sophisticated. In this article, we will explore the history of encryption, the different types of encryption techniques, and how they are used in modern cryptography.
The History of Encryption
Encryption has been used for centuries to protect information. One of the earliest recorded examples of encryption dates back to ancient Greece, where the Spartan military used a system of scytale to encrypt messages. Scytale was a wooden rod that was used to wrap a piece of parchment around. The message was then written on the parchment and when unwrapped, it appeared as gibberish. Only those with the correct wooden rod could decipher the message.
Throughout history, encryption has been used for military, political, and economic purposes. The Roman Empire used a system of substitution ciphers to protect their military and diplomatic communications. During World War II, the Germans used a sophisticated encryption machine called the Enigma to encode their messages. The Allies were eventually able to crack the Enigma code, which played a crucial role in their victory.
Types of Encryption Techniques
Encryption techniques can be broadly divided into two categories: symmetric and asymmetric encryption.
Symmetric Encryption:
Symmetric encryption, also known as shared secret encryption, is a type of encryption that uses a single key to both encrypt and decrypt data. This key must be kept secret, as anyone with the key can decrypt the data. Symmetric encryption algorithms are fast and efficient, making them suitable for encrypting large amounts of data. However, since the same key is used for encryption and decryption, symmetric encryption is vulnerable to key distribution and management issues.
One of the most widely used symmetric encryption algorithms is the Advanced Encryption Standard (AES), which is a block cipher that can use keys of 128, 192, or 256 bits. AES is considered to be highly secure and is used in many applications, including wireless networks, virtual private networks (VPNs), and encrypted email.
Another popular symmetric encryption algorithm is the Data Encryption Standard (DES), which was widely used in the 1970s and 1980s but has since been replaced by more secure algorithms such as AES. DES uses a 56-bit key and is no longer considered to be secure against modern cryptographic attacks.
Symmetric encryption is one of the most basic encryption techniques. It involves using a single key to both encrypt and decrypt data. The same key is used by both the sender and the receiver of the encrypted message. This type of encryption is also known as shared secret encryption.
One of the most commonly used symmetric encryption algorithms is the Advanced Encryption Standard (AES). It is a block cipher algorithm that uses a fixed-length key to encrypt data in blocks of 128 bits. AES has become the industry standard for symmetric encryption because of its high level of security and efficiency.
The main advantage of symmetric encryption is its simplicity and speed. It is relatively easy to implement and can encrypt and decrypt data quickly. However, the key used for encryption must be securely shared between the sender and receiver. If the key falls into the wrong hands, the encrypted data can be easily decrypted.
Symmetric encryption, also known as shared secret encryption, is a type of encryption that uses the same key to encrypt and decrypt data. The sender and receiver must share the same key, which is a secret between them. This type of encryption is fast and efficient, making it ideal for encrypting large amounts of data. However, the security of symmetric encryption is only as good as the security of the key.
One of the most commonly used symmetric encryption algorithms is the Advanced Encryption Standard (AES). AES is a block cipher encryption algorithm that uses a fixed block size of 128 bits and supports key sizes of 128, 192, and 256 bits. AES has been adopted as the standard encryption algorithm by the US government and is used worldwide to secure sensitive information.
Symmetric encryption, also known as shared secret encryption, is a type of encryption where the same key is used for both encryption and decryption. This means that both the sender and the receiver of the message must have the same key in order to communicate securely.
The most common symmetric encryption algorithm is the Advanced Encryption Standard (AES). AES is a block cipher that encrypts data in fixed-size blocks of 128 bits. It is a widely used encryption algorithm that is used to secure data in many applications, including banking, e-commerce, and military communications.
One of the main advantages of symmetric encryption is that it is fast and efficient. It is also relatively easy to implement and can be used to encrypt large amounts of data. However, the main disadvantage of symmetric encryption is that the same key is used for both encryption and decryption. This means that if the key is compromised, an attacker can easily decrypt the message.
Asymmetric Encryption:
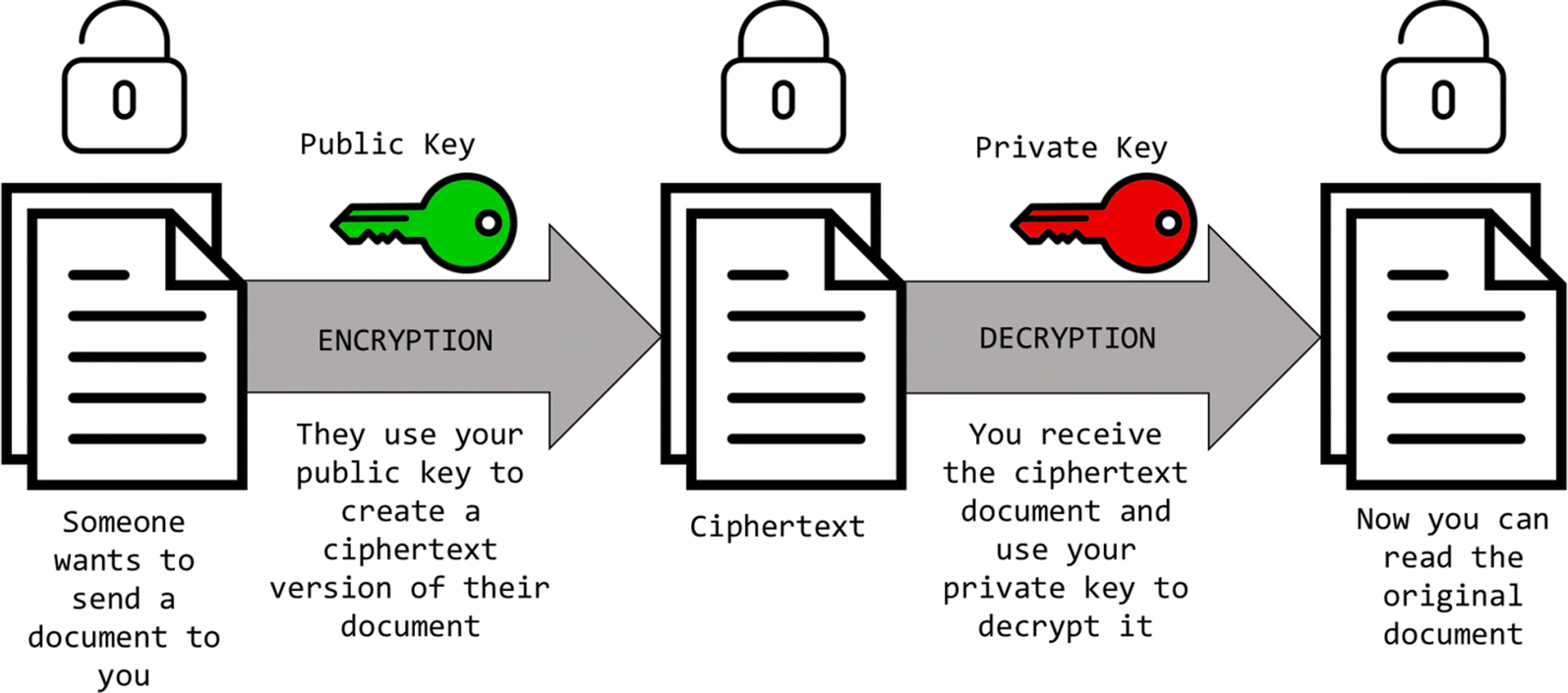
Asymmetric encryption, also known as public-key encryption, is a type of encryption that uses two keys: a public key and a private key. The public key is used to encrypt data, while the private key is used to decrypt it. Unlike symmetric encryption, the public key can be freely distributed, while the private key must be kept secret.
Asymmetric encryption algorithms are slower and more computationally intensive than symmetric encryption algorithms, but they are more secure and do not suffer from the key distribution and management issues that plague symmetric encryption. One of the most widely used asymmetric encryption algorithms is the RSA algorithm, which is named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman. RSA uses keys of typically 1024 or 2048 bits and is widely used in digital signatures, key exchange, and other cryptographic applications.
Asymmetric encryption, also known as public key encryption, is a more secure form of encryption than symmetric encryption. As the name suggests, this type of encryption involves using two different keys: a public key and a private key. The public key is used to encrypt data, while the private key is used to decrypt it.
One of the most widely used asymmetric encryption algorithms is the RSA algorithm. It uses large prime numbers to generate the public and private keys. RSA encryption is used for secure communication over the internet, such as in online banking and e-commerce transactions.
Asymmetric encryption is more secure than symmetric encryption because the private key used for decryption is never shared with anyone else. This makes it more difficult for an attacker to intercept and decrypt the data. However, asymmetric encryption is slower and more computationally intensive than symmetric encryption.
Asymmetric encryption, also known as public-key encryption, is a type of encryption that uses two keys, a public key, and a private key. The public key is used to encrypt data, and the private key is used to decrypt data. The public key is widely distributed, and anyone can use it to encrypt messages to the owner of the private key. The private key is kept secret and is only known to the owner of the key.
The most commonly used asymmetric encryption algorithm is the RSA algorithm. RSA is a public-key encryption algorithm that uses prime numbers to generate keys. RSA is widely used to secure electronic transactions, including online banking, e-commerce, and digital signatures.
Asymmetric encryption, also known as public key encryption, is a type of encryption where two different keys are used for encryption and decryption. The public key is used for encryption and is freely available to anyone, while the private key is used for decryption and is kept secret by the owner.
The most common asymmetric encryption algorithm is the RSA algorithm. RSA is based on the difficulty of factoring large prime numbers. It is a widely used encryption algorithm that is used to secure data in many applications, including email, web browsing, and online banking.
One of the main advantages of asymmetric encryption is that it provides a higher level of security than symmetric encryption. This is because the private key is kept secret and is never shared with anyone. This means that even if the public key is compromised, an attacker would not be able to decrypt the message without the private key. However, the main disadvantage of asymmetric encryption is that it is slower and less efficient than symmetric encryption.
Hash Functions:
Hash functions are a type of one-way encryption that are used to generate a fixed-size message digest or hash value from a variable-length input. The hash value is unique to the input and is used to verify the integrity of the data. Hash functions are widely used in digital signatures, message authentication codes (MACs), and other applications where data integrity is critical.
One of the most widely used hash functions is the Secure Hash Algorithm (SHA), which was developed by the National Security Agency (NSA) and is available in several variants, including SHA-1, SHA-2, and SHA-3. SHA-1 is no longer considered to be secure against modern cryptographic attacks, and SHA-2 and SHA-3 are widely used in many applications.
Hash functions are mathematical algorithms that convert data of any size into a fixed-length hash value. Hash functions are one-way functions, which means that the hash value cannot be reversed to obtain the original data. Hash functions are widely used in digital signatures, message authentication, and data integrity checking.
The most commonly used hash function is the Secure Hash Algorithm (SHA). SHA is a family of cryptographic hash functions that are widely used in digital certificates, SSL/TLS, and other security protocols.
Hash functions are a type of encryption algorithm that is used to create a fixed-length digital fingerprint of a message or file. The hash function takes the message or file as input and produces a fixed-length output, known as the hash value. The hash value is unique to the input and any changes made to the input will result in a different hash value.
Hash functions are commonly used in digital signatures, password storage, and message authentication codes. They are also used in blockchain technology to
Hash functions are a type of one-way encryption algorithm. They take an input and produce a fixed-length output, known as a hash. Hash functions are used for data integrity and authentication purposes, as well as for storing passwords securely.
One of the most commonly used hash functions is the Secure Hash Algorithm (SHA). SHA is a family of cryptographic hash functions that produce a 160-bit, 256-bit, or 512-bit hash. SHA-256 is commonly used in digital signatures, while SHA-512 is used for password hashing.
Hash functions are one-way encryption algorithms, which means that it is impossible to reverse engineer the original data from the hash. This makes them useful for password storage, as the actual password is never stored, only the hash of the password. However, because hash functions produce a fixed-length output, there is always a possibility of a hash collision, where two different inputs produce the same hash. This can be exploited by attackers to gain unauthorized access to a system.
Digital Certificates:
Digital certificates are electronic documents that are used to verify the identity of an individual, organization, or website. Digital certificates are issued by a Certificate Authority (CA) and contain information about the certificate holder, such as their name, public key, and expiration date. Digital certificates are used to secure online transactions, including e-commerce, online banking, and email communication.
Digital signatures are a way of ensuring the authenticity and integrity of digital documents. They are created using asymmetric encryption and are used to verify the identity of the sender and ensure that the contents of the document have not been altered.
To create a digital signature, the sender uses their private key to encrypt a hash of the document. The recipient then uses the sender’s public key to decrypt the hash and compare it to the hash of the received document. If the two hashes match, the document is considered authentic and unaltered.
Digital signatures are widely used in electronic documents and transactions, such as online contracts and legal
Transport Layer Security (TLS):
Transport Layer Security (TLS), formerly known as Secure Sockets Layer (SSL), is a security protocol that provides secure communication over the internet. TLS is widely used to secure online transactions, including e-commerce, online banking, and email communication. TLS uses a combination of symmetric and asymmetric encryption to secure data in transit.
- Hybrid Encryption
Hybrid encryption is a combination of symmetric and asymmetric encryption techniques. In hybrid encryption, the data is first encrypted using a symmetric encryption algorithm with a randomly generated key. This key is then encrypted using an asymmetric encryption algorithm and sent along with the encrypted data. The recipient uses their private key to decrypt the symmetric key, which is then used to decrypt the data.
Hybrid encryption combines the advantages of both symmetric and asymmetric encryption, providing strong security and efficient key management. Hybrid encryption is widely used
Conclusion:
Encryption is an essential aspect of securing sensitive information, communication, and data. There are various encryption techniques and algorithms used to protect data in transit and at rest. Symmetric encryption is fast and efficient, while asymmetric encryption provides enhanced security. Hash functions are used for digital signatures, message authentication, and data integrity checking. Digital certificates and TLS are used to secure online transactions. With the ever-increasing reliance on digital technology, encryption will continue to play a crucial role in ensuring the confidentiality, integrity, and availability of sensitive information.